|
Authenticating Users
There are several different methods that can be used to authenticate the
user when connecting to a remote host computer. In most situations, the
most convenient user authentication methods are public-key
authentication, certificate authentication or authentication with
hardware tokens (smart cards).
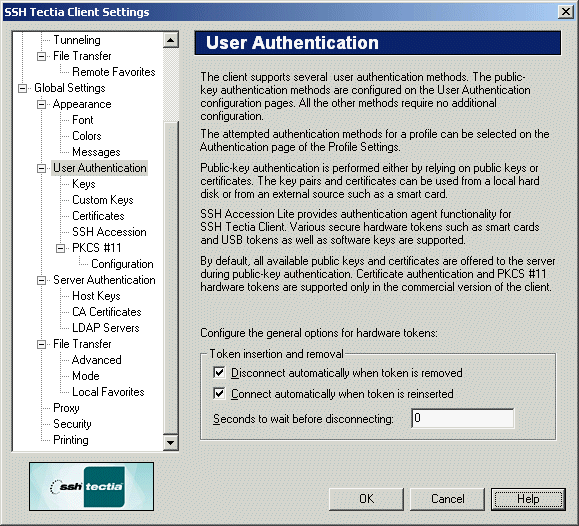
Figure : The User Authentication page of the Settings dialog
To use public-key authentication, you must upload your public
key to your home directory on the remote host computer. You also have to
modify your authorization file to allow connecting with the new
key. For more information, see Section
Manually Editing the Authorization File. By default, all available public
keys and certificates are offered to the remote host computer during
public-key authentication.
Certificate authentication is more secure than the traditional
public-key authentication, as the system verifies that the user
certificate has been issued by a trusted certification authority (CA) and
that the certificate has not been revoked. Certificate authentication is
also more convenient, as no local database of users' public keys is
required on the remote host computer.
Probably the most convenient method is to use a hardware token (smart
card) that must be inserted into a card reader device to authenticate
the user.
Token Insertion and Removal
The following options specify how hardware tokens are used for user authentication:
- Disconnect automatically when token is removed
Select this check box to immediately terminate the connection if your
token is removed from the card reader device. This ensures that a
connection will be active only when a token is inserted.
- Connect automatically when token is reinserted
Select this check box to automatically reconnect when your token is
inserted into the card reader device. This check box is active only if the
Disconnect automatically when token is removed check box is
selected.
- Seconds to wait before disconnecting
In the text field you can specify how many seconds the connection will
remain open if your token is removed from the card reader device. The
default value is zero. This field is active only if the Disconnect
automatically when token is removed check box is selected.
 [Contents]
[Index]
[Contents]
[Index]
[ Contact Information | Support | Feedback | SSH Home Page | SSH Products ]
Copyright © 2010 SSH Communications Security Corp.
This software is protected by international copyright laws. All rights reserved.
Copyright Notice
|