|
Managing CA Certificates
On the CA Certificates page of the Settings dialog you
can manage the certificates of your trusted certification authorities
(CA). For more information on certificates, see SSH Tectia
Client/Server Product Description.
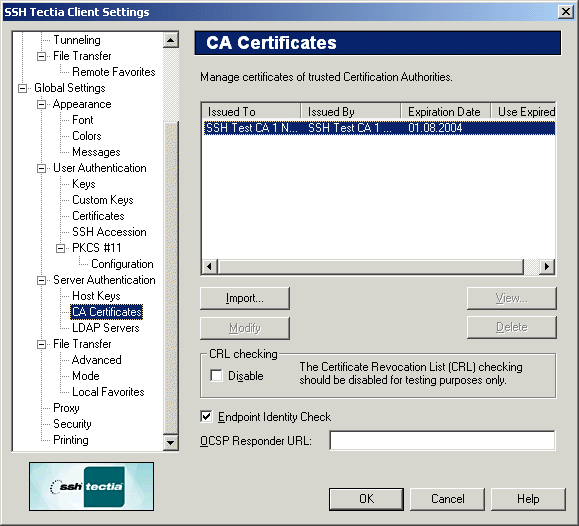
Figure : Trusted Certification Authorities
CA certificate list
The available CA certificates are shown on the CA certificate list at
the top of the CA Certificates page.
The following fields are displayed on the CA certificate list:
- Issued To
The Issued To field shows the certification authority to whom
the certificate has been issued.
- Issued By
The Issued By field shows the entity who has issued the CA certificate.
- Expiration Date
The Expiration Date field shows when the CA certificate will expire.
- Use Expired CRLs
This field shows how long expired CRLs are used (time in seconds).
Buttons:
The following buttons can be used to manage the CA certificates:
- Import...
Click Import... to import a CA certificate from an
external file. The Import Certificate - Select File dialog
opens, allowing you to locate the certificate file.
- View...
Click View... to display the contents of the selected CA
certificate.
- Modify
Click Modify to edit the selected CA certificate.
- Delete
Click Delete to remove the selected CA certificate.
CRL Checking
Select the Disable check box to prevent the use of a
certificate revocation list (CRL). A CRL is used to check if any of the
used server certificates have been revoked.
Note: Disabling CRL checking is a security risk and should be
done for testing purposes only.
Endpoint Identity Check
Specifies whether the client will verify the server's hostname against the
Subject Name or Subject Alternative Name (DNS Address) in the server's
certificate.
If this check box is not selected, the fields in the server host
certificate are not verified and the certificate is accepted based on
validity period and CRL check only. Note that this is a possible security
risk, as anyone with a certificate issued by the same trusted CA that
issues the server host certificates can perform a man-in-the-middle attack
on the server if a client has the endpoint identity check disabled.
OCSP Responder URL
The OCSP Responder Service provides client applications a
point of control for retrieving real-time information on the validity
status of certificates using the Online Certificate Status Protocol
(OCSP). For more information on OCSP, see RFC 2560.
 [Contents]
[Index]
[Contents]
[Index]
[ Contact Information | Support | Feedback | SSH Home Page | SSH Products ]
Copyright © 2010 SSH Communications Security Corp.
This software is protected by international copyright laws. All rights reserved.
Copyright Notice
|