|
Defining Security Settings
The security settings can be configured using the Security page
of the Settings dialog.
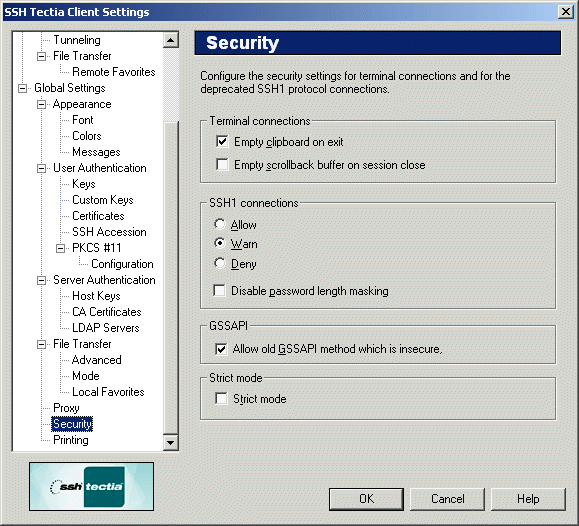
Figure : The Security page of the Settings dialog
Terminal Connections
- Empty Clipboard on Exit
Select the Empty Clipboard on Exit check box to remove anything
that was recently copied using the cut and paste operations from the
clipboard.
- Empty Scrollback Buffer on Session Close
Select the Empty Scrollback Buffer on Session Close check box
to empty any remains of the terminal output from the scrollback buffer.
SSH1 Connections
You can also connect to Secure Shell protocol version 1 (SSH1) servers.
With the SSH1 Connections selection you can allow SSH1
connections, deny them, or issue a warning when connecting to a remote
host computer that is using version 1 of the Secure Shell protocol.
Secure Shell protocol version 2 (SSH2) is a more advanced
and secure protocol than the legacy version SSH1. SSH Communications
Security considers the SSH1 protocol deprecated and does not recommend
its use anymore.
Note that when using an SSH1 connection, multiple terminal windows and
the file transfer operations are not available.
- Allow
Select this option to allow also SSH1 connections.
- Warn
Select this option to issue a notice when an SSH1 connection is made.
- Deny
Select this option to deny SSH1 connections.
These setting affects the GUI client (only). See Section
ssh2_config for instructions on disabling the
SSH1 compatibility with the command-line client.
GSSAPI
If Allow old GSSAPI method wich is insecure is selected, GSSAPI
authentication will fall back to the old GSSAPI method (without Message
Integrity Code) if the new GSSAPI method (with MIC) fails.
 [Contents]
[Index]
[Contents]
[Index]
[ Contact Information | Support | Feedback | SSH Home Page | SSH Products ]
Copyright © 2010 SSH Communications Security Corp.
This software is protected by international copyright laws. All rights reserved.
Copyright Notice
|