|
Authentication
The Secure Shell protocol used by SSH Tectia Server for IBM z/OS provides mutual authentication
– the client authenticates the server and the server authenticates the
client user. Both parties are assured of the identity of the other party.
The Secure Shell server host can authenticate itself using either
traditional public-key authentication or certificate authentication.
Different methods can be used to authenticate Secure Shell client users.
These authentication methods can be combined or used separately,
depending on the level of functionality and security you want.
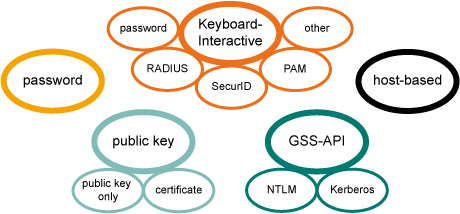
Figure : Secure Shell user authentication methods. Note that all of the methods are not available on z/OS.
The SSH Tectia client on z/OS uses the following user authentication methods
by default (in order): public-key, keyboard-interactive, and password
authentication. In addition, the client supports host-based
authentication.
The SSH Tectia server on z/OS allows public-key and password authentication by
default. In addition, the server supports keyboard-interactive and host-based
authentication.
 [Contents]
[Index]
[Contents]
[Index]
[ Contact Information | Support | Feedback | SSH Home Page | SSH Products ]
Copyright © 2007 SSH Communications Security Corp.
This software is protected by international copyright laws. All rights reserved.
Copyright Notice
|