|
Connection Parameters
The Connect to Remote Host dialog allows you to specify the host
name (or IP address), user name, port number, and authentication method
for the new connection.
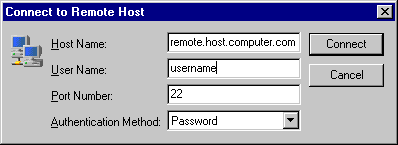
Figure : Identify yourself to the remote host computer
The client remembers your previous connection if you saved the settings
before closing the connection. If you are going to reconnect to the same
host, you do not have to type in the same information again.
- Host Name
Enter the name (or IP address) of the remote host computer in this field.
Unless this is your first connection, the Host Name field shows
the name used in the previous connection. If you want to connect to the
same computer as previously, you do not have to edit this field.
- User Name
Enter your user name as used in the remote host computer. Unless this is
your first connection, the User Name field shows the name used in
the previous connection. If you want to connect using the same user name
as previously, you do not have to edit this field.
- Port Number
Type the number of the port used in the connection in this field. The
standard port for Secure Shell connections is 22. The port used in the
previous connection is already filled in.
- Authentication Method
Select the desired authentication method from the drop-down menu. Possible
authentication methods are Password, Public Key,
SecurID (legacy), PAM (legacy), Keyboard
Interactive, GSSAPI, and <Profile Settings>.
- Password
When you login using password authentication, you will have to type your
password each time you establish a new connection to the remote host
computer.
- Public Key
Public-key authentication is based on the use of digital
signatures. If you want to use public-key authentication, first
you need to create a pair of key files. See Section Generating Keys.
Before you can log in using public-key authentication, you have to upload
your public key to the remote host computer. See section Uploading Your Public Key.
For more information on the use of public keys, see Section Using Public-Key Authentication.
- SecurID (legacy)
Using SecurID authentication requires that you have a SecurID device that
generates the numeric codes that are needed to login. The legacy method is
supported for interoperability reasons. It is recommended to use the
Keyboard-Interactive method instead.
- PAM (legacy)
The Pluggable Authentication Module (PAM) is an authentication method that
has gained wide popularity especially on Unix platforms. The legacy method
is supported for interoperability reasons. It is recommended to use the
Keyboard-Interactive method instead.
- Keyboard-Interactive
Keyboard-Interactive is designed to allow the Secure Shell client to
support several different types of authentication methods. For more
information on Keyboard-Interactive, see SSH Tectia Client/Server
Product Description.
- GSSAPI
GSSAPI (Generic Security Service Application Programming Interface)
allows different security mechanisms to be used via one standardized
API. For more information on GSSAPI, see SSH Tectia Client/Server
Product Description.
- <Profile Settings>
The authentication method specified in the active profile is used. The
profile-specific authentication method can be defined using the
Connection page of the Settings dialog
(see Section Defining Connection Settings).
- Connect
Click this button to connect to the remote host computer.
- Cancel
Click this button to cancel the connection.
 [Contents]
[Index]
[Contents]
[Index]
[ Contact Information | Support | Feedback | SSH Home Page | SSH Products ]
Copyright © 2010 SSH Communications Security Corp.
This software is protected by international copyright laws. All rights reserved.
Copyright Notice
|
 |