 |
|
Introduction to Transparent FTP Security
Transparent FTP tunneling and FTP-SFTP conversion can be used to
secure both interactive and unattended FTP sessions. They provide a quick and
easy way to secure FTP file transfers without the need to change existing
FTP jobs or scripts.
- Transparent FTP tunneling
Transparent FTP tunneling is implemented using the SSH Tectia SOCKS Proxy
component. SSH Tectia SOCKS Proxy acts as a SOCKS proxy for the FTP client application on
the SSH Tectia Server for IBM z/OS host and captures FTP connections based on filter rules. The
tunneling is transparent to the user and the FTP application. The only
change needed in the FTP application is to change the SOCKS proxy setting to
point to a localhost listener.
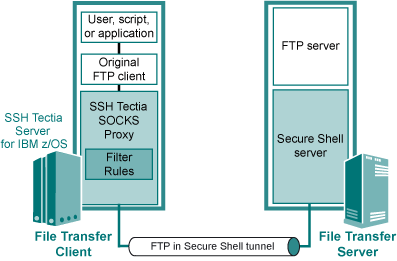
Figure : The architecture of transparent FTP tunneling
The SOCKS Proxy uses the hostname, username, and password information
provided by the FTP client application to open an authenticated and
encrypted tunnel to a Secure Shell server. Alternatively, public-key
authentication can be used for opening the tunnel
The Secure Shell server can also defined in the filter rules. In this
case, the secure tunnel is terminated at the Secure Shell server and from
there the FTP connection is forwarded to the FTP server unsecured.
- FTP-SFTP conversion
FTP-SFTP conversion is implemented using the SSH Tectia SOCKS Proxy
component. SSH Tectia SOCKS Proxy acts as a SOCKS proxy for the FTP client application on
the SSH Tectia Server for IBM z/OS host and captures FTP connections based on filter rules. FTP
connections are converted to SFTP, transparently to the user and the FTP
application. The only change needed in the FTP application is to change the
SOCKS proxy setting to point to a localhost listener.
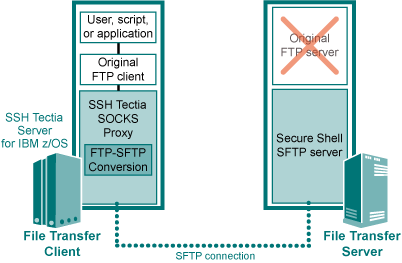
Figure : The architecture of FTP-SFTP conversion
The SOCKS Proxy uses the hostname, username, and password information
provided by the FTP client application to open an authenticated and
encrypted SFTP connection to a Secure Shell SFTP server. Alternatively,
public-key authentication can be used for opening the SFTP
connection.
The Secure Shell SFTP server can also defined in the filter rules.
This way, the client's request for the FTP server destination can be
overridden.
To enable transparent FTP tunneling and FTP-SFTP conversion, you need to
complete the following tasks:
- Configure the SSH Tectia SOCKS Proxy to listen on port 1080 on the client
host and define the filter rules in the
ssh-socks-proxy-config.xml
configuration file. See Section Configuring SOCKS Proxy.
- Create a user, for example
SSHSP, for running the SOCKS Proxy.
See Section Creating the SSHSP User.
- Start the
ssh-socks-proxy process.
See Section Running SSH Tectia SOCKS Proxy.
- (Optional) If you want to use public-key authentication with
passphrase-protected keys, use the
ssh-socks-proxy-ctl tool to give the
passphrases to the keys and load the keys in the memory. See Section Using Public-Key Authentication with the SOCKS Proxy.
- Configure the SOCKS settings for the FTP client.
See Section Configuring FTP.
After these tasks are completed, the specified FTP connections will be
automatically tunneled or converted to SFTP, transparently to the user.
 [Contents]
[Index]
[Contents]
[Index]
[ Contact Information | Support | Feedback | SSH Home Page | SSH Products ]
Copyright © 2011 SSH Communications Security Corp.
This software is protected by international copyright laws. All rights reserved.
Copyright Notice
|
 |
|