 |
|
Using Public-Key Authentication from Windows Client to z/OS Server
The instructions apply to SSH Tectia Client 5.1 and later. For more information, see
SSH Tectia Client 5.x User Manual.
Using Graphical User Interface
On Windows, you can use the SSH Tectia Key Generation wizard to generate a key
pair.
- New keys are generated in the SSH Tectia Configuration tool. Select the
Keys and Certificates page under User authentication and
click New Key... to start the Key Generation wizard.
The wizard will generate two key files, your private key and your
public key. The private key file has no file extension, and the public key
has the same base file name as the private key, but with
.pub
as the file extension. The key files will be stored on your local
computer, in the user profile directory.
- Public keys can be uploaded automatically to servers that have the
SFTP subsystem enabled. The automatic upload can be done on the Keys and
Certificates page of SSH Tectia Configuration tool.
Select your key pair from the list and click Upload. The Upload
Public Key dialog box opens.
- Define the conversion parameters directly in the Destination folder path
as shown in Figure Uploading the public key below.
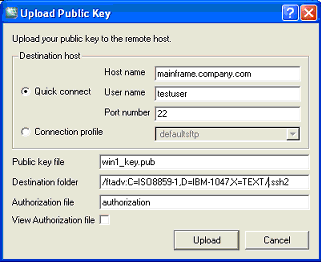
Figure :
Uploading the public key
Click Upload to start the upload.
- If you are already connected to the remote server host, the key upload
starts immediately. If you are not connected, you will be prompted to
authenticate to the server (by default with password).
- Make sure that public-key authentication is allowed in the Connection Broker
configuration on Client, in the default settings and in the
relevant connection profile (it is allowed by default).
Using Command-Line Tools
The key pair can also be generated and transferred to the z/OS server by
using command-line tools.
- Create a key pair using
ssh-keygen-g3. For non-interactive
use, the key can be generated without a passphrase with the -P
option.
C:\>ssh-keygen-g3 -t rsa -b 1024 -P win_key
Generating 1024-bit rsa key pair
2 Oo.oOo.oOOo.
Key generated.
1024-bit rsa, user1@TESTWIN, Fri Aug 25 2006 07:59:40
Private key saved to C:\Documents and Settings\user1\Application Data\
SSH\UserKeys\win_key
Public key saved to C:\Documents and Settings\user1\Application Data\
SSH\UserKeys\win_key.pub
|
- Transfer the public key with conversion options.
C:\>scpg3 "C:\Documents and Settings\user1\Application Data\SSH\UserKeys\
win_key.pub" user1@zos:/ftadv:C=ISO8859-1,D=IBM-1047/.ssh2/
- Create the remote authorization file.
C:\>sshg3 user1@zos "echo Key win_key.pub >> .ssh2/authorization"
- Make sure that public-key authentication is allowed in the Connection Broker
configuration on Client, in the default settings and in the
relevant connection profile (it is allowed by default).
 [Contents]
[Index]
[Contents]
[Index]
[ Contact Information | Support | Feedback | SSH Home Page | SSH Products ]
Copyright © 2006 SSH Communications Security Corp.
This software is protected by international copyright laws. All rights reserved.
Copyright Notice
|
 |
|